CYREBRO 2022 Predictions
- Intro
- 1. Tracking the attack chain will become a top priority:
- 2. Vulnerability management will be overhauled
- 3. Multi-factor authentication will no longer be enough
- 4. 2022 will prompt artificial intelligence, machine learning security audits
- 5. Investment will pour into DevOps with less focus on general IT budget
- 6. UEBA (user entity behavior analytics) will play a greater part in enterprise protection
- 7. Business Email Compromise (BEC) scams will continue to surge
- Key takeaways
The time for blind trust in security solutions is over
Just because something was secure in the past does not mean it is going to be secure in the future. Centralized security mechanisms and improved visibility, enhanced authentication protocols, and reducing the complexity of existing security solutions are now all critical to protecting corporate networks.
1. Tracking the attack chain will become a top priority
Modern threat actors have a wider potential attack surface than ever before. Employee devices, email accounts, open-source components and libraries, fake or compromised security certificates, third-party software, and vulnerabilities in existing enterprise systems are some, but not all, of the options available as avenues for attack.
Implementing continuous networking monitoring and improving visibility into core processes will become a top priority for businesses in 2022.
2. Vulnerability management will be overhauled
Blind trust in the processes managing security patches cannot continue. As the recent sabotage of the SolarWinds Orion update highlights, if a central vendor at the heart of software deployment is compromised, the ramifications can be severe for every customer down the supply chain.
It was once the case that neglecting to update software builds or apply security patches in good time was the major risk factor — but now, the attack chain can even start with a trusted service provider.
CYREBRO predicts that organizations taking their security posture seriously will overhaul existing patch management systems over 2022 and may implement changes including sandboxed checks during the process, enhancing audits, or imposing additional checks for other vulnerabilities or weaknesses to prevent disruption to the CI/CD process.
The increased exploitation of zero-day vulnerabilities and unpatched N-day bugs was a major trend in 2021 and this will certainly continue in the future.
3. Multi-factor authentication will no longer be enough
Two-factor authentication (2FA) and multi-factor authentication (MFA) are not as safe as they used to be and cannot, any longer, be considered the magic solution for account and network protection.
2FA/MFA protections may include a secondary code that is sent to a mobile device or email address to verify an account holder’s identity, a tap required with a physical security key such as a YubiKey, the use of Authenticator apps, or the submission of a biometric marker including a face scan or fingerprint.
However, with every new security measure developed and employed, threat actors will try to overturn them.
Modern attack methods include bypassing or hijacking sessions to obtain authentication tokens; using social engineering to launch SIM-swapping attacks, attempts to brute force and guess 2FA codes when online services are vulnerable to automated attacks, the exploitation of vulnerabilities in MFA/2FA platforms, and Man-in-The-Middle (MiTM) attacks against channels tasked with handling authentication processes.
CYREBRO predicts that more attack methods will evolve to bypass 2FA and MFA in the future, and the only way to mitigate the risk of new methods is to implement secondary authentication in the most secure ways possible and to not consider them your only security boundary, but rather one element of network defense.
4. 2022 will prompt artificial intelligence, machine learning security audits
As the enterprise continues to adopt machine learning and artificial intelligence cybersecurity solutions, there cannot be blind faith in either the datasets or algorithms used — and so in 2022, security audits will not only have to apply to corporate networks but also the underlying ML and AI processes in play to protect them.
CYREBRO expects that as we become more aware of the value of ML and AI, the spotlight will also shine on the inherent security issues of these new technologies.
These include poisoning data lakes to generate inaccurate results or false positives; inherent biases in algorithmic programming, and attackers misleading these solutions to provide malicious outputs by tampering with existing, online systems and the data they produce.
Adversarial machine learning is an emerging threat that needs to be tackled now to mitigate the risk of ML/AI platforms becoming compromised. In Deloitte’s State of AI in the Enterprise survey, executives said that AI initiatives are key to remaining competitive in the next five years, but AI solutions also require oversight and maintenance to ensure ongoing quality and ROI.
CYREBRO predicts that adversarial machine learning-based attacks will escalate in the near future and as more evidence surfaces of this trend, security checks will have to apply to AI and ML — whether or not these systems are protecting networks in turn. It is also possible that regulatory discussions and proposals concerning the control and security of these technologies will surface in 2022.
5. Investment will pour into DevOps with less focus on general IT budget
CYREBRO predicts that in 2022 and beyond, enterprise players will invest more into DevOps, with a greater emphasis placed on continuous application delivery securely and reliably
As companies continue to shift to hybrid working, cloud environments, SASE, and SaaS services designed to replace legacy, on-premise setups, DevOps teams play a critical role in the continual delivery of services and integration which does not cause business disruption.
Less weight and focus will be placed on general IT and investment will shift to DevOps solutions that can streamline and cut down development lifecycles, as well as securely manage the deployment of new code, patches, and systems.
6. UEBA (User Entity Behavior Analytics) will play a greater part in enterprise protection
User and entity behavior analytics (UEBA) solutions utilize machine learning algorithms and data sets to monitor and analyze network events generated by users. Anomalies in typical usage and access patterns are then flagged as potentially suspicious, alerting SOC teams to investigate potentially malicious activity further.
UEBA can be leveraged to monitor both human and machine ‘entity’ activity on a network and as it focuses on behavioral patterns, UEBA may be able to quickly flag the use of compromised credentials, the lateral movement of threat actors, and potential cybersecurity incidents caused by insiders or machine entities that are no longer operating in the way they should.
CYREBRO expects further development in this field as we move away from reliance on traditional scanning protocols and as we harness new technologies to reduce the workload of human teams.
The UEBA market is expected to increase from an estimated $131.7 million in 2016 to $908.3 million by 2021.
7. Business Email Compromise (BEC) scams will continue to surge
BEC fraud is a form of spear phishing, in which cybercriminals will conduct social engineering and reconnaissance against a target before initiating contact. Most often, BEC scammers will target a victim organization’s accountancy, invoice, and payroll staff with emails crafted to appear legitimate.
If employees are duped, they may end up signing off fake payments or sending funds to bank accounts owned by criminals. In sophisticated BEC attacks, threat actors may compromise existing communication chains to covertly alter bank account details, before vanishing with payments intended for legitimate suppliers, payroll, or service providers.
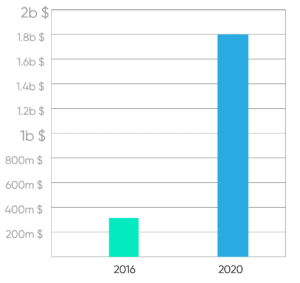
The FBI has warned that BEC scams are increasing year over year, with reported rates doubling between 2018 and 2019, moving from $360 million in 2016 to a staggering $1.8 billion in 2020, according to the Internet Crime Complaint Center (IC3).
Recapping 2021
High-profile ransomware attacks, data breaches, and cyberattacks launched against core utilities and public services have dominated the headlines over 2021.
We have recently experienced cataclysmic shifts in the way we work and in how businesses are managed. A ripple effect of the coronavirus pandemic, a new reliance on remote setups, has also exposed gaps in network visibility and how best to manage endpoints connecting to corporate resources.
Cyber attackers are constantly evolving and refining their attack methods. Over the past year, CYREBRO has seen the following trends in how cyber attackers obtain access to enterprise networks.
Phishing
One of the oldest tricks in the threat actor book is phishing. Fraudulent emails, malicious social media content, and SMS messages are sent to prospective victims to entice them into clicking on fraudulent links or to download malware payloads. At the lowest levels of sophistication, phishing messages are sent en masse with subjects ranging from romance to loans, insurance, COVID-19, or they may display fake banking alerts.
At higher levels, you may encounter spear phishing, a more time-consuming endeavor requiring social engineering, research, and tailored communication to compromise targets selected on an individual basis, a common tactic employed by business email compromise (BEC) fraudsters.
Vulnerability exploits
2021 highlighted how devastating zero-day and unpatched vulnerabilities in popular platforms can be.
The Microsoft Exchange Server attacks, for example, were caused by in-the-wild exploitation of the ProxyLogon 0-days, leading to the compromise of thousands of on-prem Exchange servers despite the release of emergency patches.
According to Risk Based Security, over 12,500 vulnerabilities were reported during the first half of 2020, and close to 1,500 of these were remotely exploitable.

Supply chain attacks
While a relatively new entry, sophisticated threat actors have pivoted to attacks against centralized systems and platforms to reach the widest possible victim pools — spending their time and energy on breaking the defenses of one vendor, and thereby potentially gaining access to IT systems belonging to customers.
The most notable in recent times is the SolarWinds supply chain incident. Russian cyberattackers were able to compromise the software vendor’s platform and deploy a malicious Orion software update to roughly 18,000 customers.
Those responsible then used the backdoors planted in the clients’ systems through the malware-laden update to directly attack the most valuable customers, including Microsoft, FireEye, and various US government agencies.
Weak authentication
Weak and stolen credentials, including those used to access multiple online services, are now a common entry point for today’s cyber attackers.
Year after year, credential-stuffing attacks are used to infiltrate the networks of enterprise players and SMBs, and yet, 76% of employees in the Fortune 1000 still reuse passwords across personal and professional accounts. The open sale and trade of data dumps on the Dark Web, sometimes available for just a few dollars, means that cybercriminals can use automated tools to strike login systems with little effort.
To make matters worse, two-factor and multi-factor authentication (2FA/MFA) standards are no longer enough, due to a variety of modern techniques and tactics actively used by modern-day attackers to circumvent these extra security barriers.
The human factor
One of the weakest links in the security chain, and one often exploited by cyber attackers, is the human factor. Bring-Your-Own-Device (BYOD) practices, shadow IT, human error, lax privilege controls, and a lack of both training and cybersecurity awareness in employees can all contribute to a weakened security posture.
Hardly a week goes by when we don’t hear of someone falling for a BEC phishing scam and losing their employer’s money, or of credentials used by an employee on a third-party service — who may have high or administrator-level privileges — that were stolen and then used to deploy ransomware on a corporate network.
Insider threats, too, are an attack vector that needs to be considered. Malicious or negligent employees, staff members that have been bribed, rogue business partners, and unethical vendors could become a future catalyst for a cybersecurity incident.
Recent examples include an employee who deleted close to 120,000 records of a company after being let go; a BUPA staff member who stole and tried to sell customer PII on the Dark Web, and even scientists who hijacked a supercomputer in their lab to mine for cryptocurrency.
It should be noted, however, that humans also have an important role in mitigating security incidents, reducing risk, and managing threat response. AI, ML, and automation are valuable tools that are quickly becoming necessary assets to fend off today’s threat actors, but human expertise, reasoning, and intuition are also crucial.
Key takeaways
When multiple InfoSec tools from different vendors are in play, it can be near-impossible for cybersecurity teams to have the means to accurately and efficiently manage threat alerts, patch processes, and to maintain a robust security posture for their organization.
Cybersecurity should be considered a right, not a privilege. As such, investment into solutions that can transform chaos into clarity, as well as improving employee awareness, will be critical when facing threats into 2022 and beyond.