Disaster Recovery vs. Cyber Recovery – Different Plans Preparing for Different Struggles

As Bob Dylan so eloquently said in his classic song from the 1960s, “Times they are a-changin,” sixty years later they still are. Modern society has grown accustomed to change. It’s the pace of it that can cause you to catch your breath at times. Just as the bulk of rock and country music is created from the simplicity of just three chords, it wasn’t long ago that enterprises were as simple as a single on-prem datacenter. Complexity back then may have involved the addition of a couple of site locations connected through static VPN.
Complexity today is completely redefined. Today’s modern enterprises are often a conglomerate of multiple clouds and edge locations that make up a vast IT estate. While organizations have done a phenomenal job adapting to remote work strategies over the past two years, many are relying on recovery strategies that aren’t designed for the complex enterprises of today.
What Is a Disaster Recovery?
With an opening like this, you’re probably anticipating an article about Disaster recovery (DR). If so, you’re partially right. Disaster recovery strategies are about preserving businesses continuity. That’s essential today because the world expects your network to be accessible in a 24/7 globally connected world. User expectations are another thing that has changed. You can’t afford to not be connected to the digital world. Disaster recovery is about extending the geographic reach of your enterprise. In the event of a natural disaster that rips through one of your physical infrastructure sites, a DR system can automatically spin up a set of mirrored assets in another location to ensure that the show goes on for your organization. As important as Disaster recovery is, however, it’s only part of the equation.
Disaster Recovery Is a Macro Tool, Not Micro
A Disaster Recovery strategy is designed to get you through the unthinkable. A tornado, flood, regional power loss, or internet outage are classic examples. While these are circumstances that must certainly be planned for, these macro-like events are fortunately infrequent. It is far more likely that your enterprise will suffer a micro event such as a data volume failure, the deletion of a critical file, or a server malfunction. Such events are addressed more efficiently by a localized backup solution as a DR strategy is completely cost-prohibitive for micro-level incidents. Restoring the data lost to a failed data volume with a DR strategy would be like eliminating an anthill with a bazooka.
What Is a Cyber Recovery Plan?
Because of the ever-increasing threats from external threat actors, there is another type of recovery needed today. Cybersecurity recovery introduces the extra steps of threat remediation and security confirmation before the process of restoring begins. Data restoration efforts are completely wasted if the threat actors still have access to the digital environment, and DR replication and synchronization processes will simply spread the malware infection to the recovery points, making them useless as well. In addition, cybersecurity recovery involves post-incident tasks such as evidence collection and root cause analysis in order to gain the understanding necessary to protect against similar threats in the future.
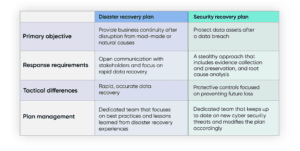
The Need for a Cyber Recovery Plan
Disaster recovery is only one piece of the recovery puzzle. Enterprises must protect themselves against a multiplicity of disrupting events, which is why companies must also employ a cyber recovery plan in addition to DR. While DR is about restoring the services of a given location, cyber recovery is about restoring a system or data environment to a point in time. This earlier point could be a state prior to the deletion of a database file or the malicious encryption of a file directory. While DR is about recovering operations through the switchover to a new location, cyber recovery is about restoring the assets residing in the primary production environment. The end objective is to restore the data successfully with minimal cost and effort and get things going again as quickly as possible.
Securing Your Cyber Recovery Repository
When it comes to ransomware and other types of malware attacks, there is often a skirmish that occurs prior to the actual battle. The skirmish entails the backup repository of a targeted organization. That’s because the backup is the last line of defense for enterprises today, which is why threat actors target it for the initial attack. Take out the backups, and an organization is at the mercy of a ransomware gang. Ransomware gangs and external threat actors, in general, are highly educated in backup system technology. In fact, they may even understand the backup system better than the organizations they target.
Securing your backups is an essential part of a zero-trust network. At the very least your backup system should be air-gapped from your production environment. Preferably, it should reside in its own firewall zone where it can be protected by firewall policies, malware scrubbers, and intrusion protection systems (ISP). While your primary backups should reside on-premise to speed and simplify your recovery efforts, you should also create secondary backups as well and store them in a secure cloud environment.
Don’t Virtualize Your Backup Servers
It’s instinctive to create a virtual server for every server need today, which is why external actors target the virtualization infrastructure. That’s where the servers are. For instance, if an attacker manages to take out the vCenter server and encompass ESX servers within your VMware environment, your backup server is out of commission as well. That’s why you need a physical server or backup appliance to host your backup system and protect the data, applications, and services hosted on your virtual servers. In addition to your backups, you also need to document the root passwords of your ESX servers and other infrastructure devices.
The Need for a Dynamic Cyber Recovery Plan
Remember the earlier inference in this article to how things are constantly changing today? Technology is constantly changing as are cyberattack methodologies. You need to ensure that your cyber recovery strategy is agile enough to adapt to the inevitable changes that will occur within your enterprise. Just as cybersecurity is a moving target, your cyber recovery strategy should be updated when needed to accommodate new technologies and protect against new emerging threats.
Conclusion
While disaster recovery and cyber recovery each have different purposes and utilize different methodologies and systems, they are both part of a larger security objective. That is to ensure the confidentiality, integrity, and availability of your enterprise systems and data assets. No one thinks much about backups, until the time you need them. Backups are about reducing your risk exposure. Make sure you have all of the components in place to protect yourself from the known risks to your organization and recover from their aftermaths.


