-

Domain Validation: Why Surface-Level Checks Aren’t Enough
It is one of the oldest concerns of conducting business transactions: How can you be sure that the other person is who they say they are. In the past, business validation was more straightforward. Customers could visit physical stores or financial centers, visually confirming the establishment’s legitimacy. Personal interactions, such as eye contact or handshakes,…
-

Securing the Heart of Your Business: Protecting Microsoft 365 and Google Workspace from Cyber Threats
During World War I, the French Prime Minister, George Clemenceau said that “generals always prepare to fight the last war.” The problem of course is that the last war used the last war’s technology which is why each subsequent war has such devastating casualties. The new attack methodologies always seem to outflank the defenses. The…
-

How Comprehensive Logging Can Stop the Next Big Cyberattack
Imagine logging into your organization’s system one morning only to discover threat actors had exfiltrated all of your current and past customers’ data. Or picture trying to log on and realizing hackers have locked you out of your systems. Although these two situations are hypothetical, the story is all too familiar. In the last few…
-
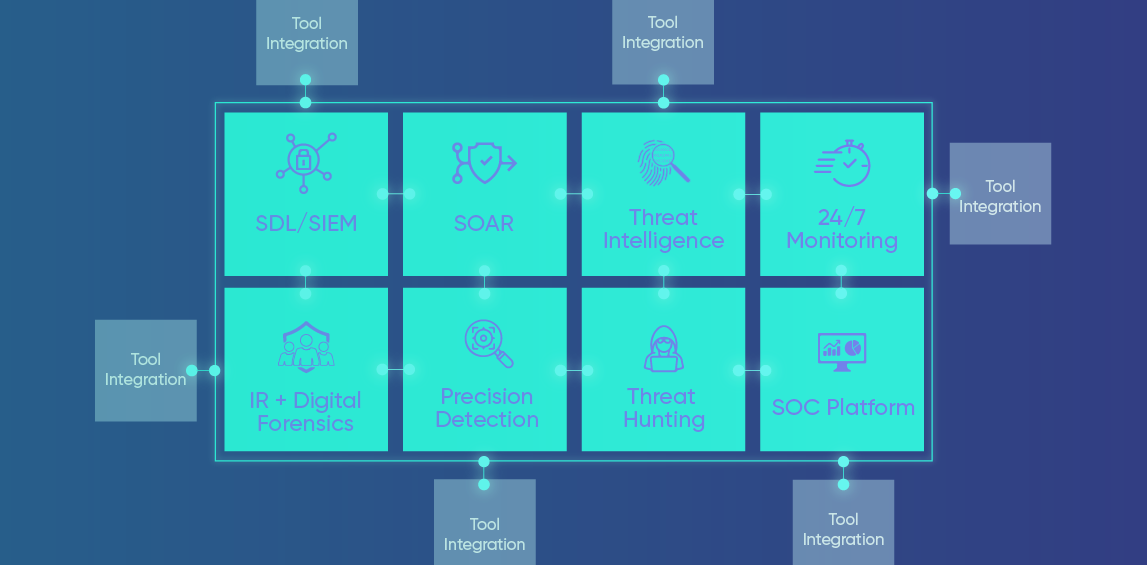
The Evolution of SecOps: The Essential Components of MDR
As threat actors launch more sophisticated and AI-enhanced attacks, traditional preventative measures alone are falling short. Adequately protecting an intricate web of modern infrastructure — a blend of on-premise and cloud-based systems, numerous mobile devices, and many applications — while navigating increasingly stringent compliance regulations demands a more proactive and holistic approach. Plenty of cybersecurity…
-

Should Your Security Solution Be Agent-Based or Agentless?
Agent-based or Agentless Security? This has been a longstanding debate among IT professionals. It is a hot topic that has gained more prominence in the cybersecurity community following the well-publicized CrowdStrike incident that disrupted computers globally. But what exactly is an agent, and how can security be managed without one? Before delving into the specifics…
-

The Security Data Lake Revolution – Ditching SIEM for Advanced Threat Detection
The relentless march of technological evolution ensures that today’s cutting-edge innovations will inevitably give way to tomorrow’s superior alternatives. While these old technologies continue to be used by some, almost everyone eventually moves on. DVD players, once ubiquitous, have been largely replaced by streaming services, yet some still maintain personal libraries. While some older generations…
Loading