-
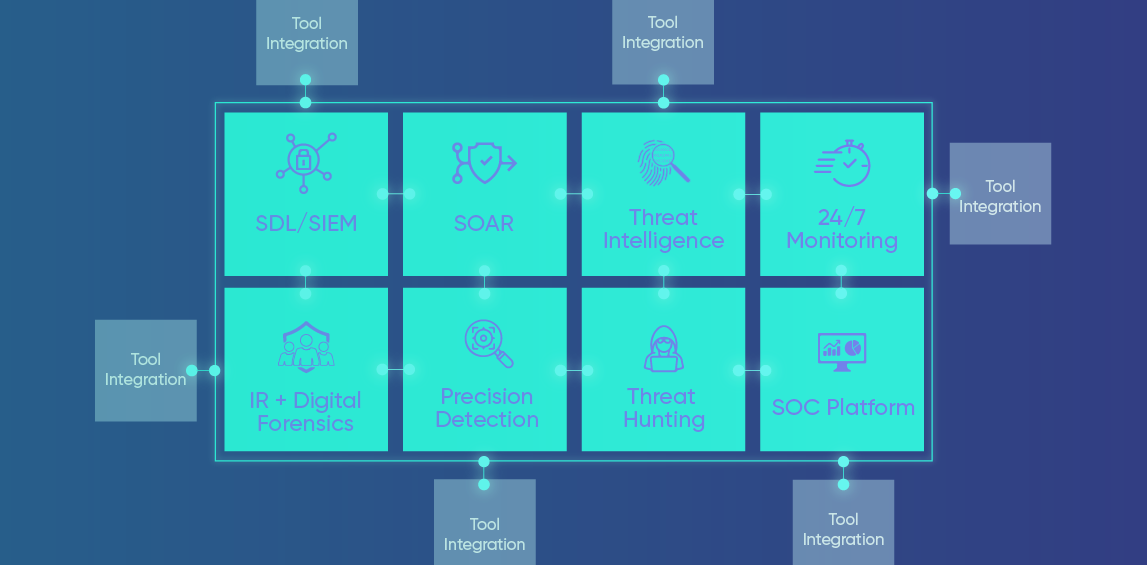
The Evolution of SecOps: The Essential Components of MDR
As threat actors launch more sophisticated and AI-enhanced attacks, traditional preventative measures alone are falling short. Adequately protecting an intricate web of modern infrastructure — a blend of on-premise and cloud-based systems, numerous mobile devices, and many applications — while navigating increasingly stringent compliance regulations demands a more proactive and holistic approach. Plenty of cybersecurity…
-

Beyond Patch Management: The Hidden Danger of Network Scans
Police officers, during a blackout, often check if a neighborhood has regained power by spotting the faint glow of doorbells. This tiny beacon of light, even in an empty house, indicates the restoration of electricity. Similarly, criminals employ surprisingly simplistic methods to identify potential targets. For instance, car thieves casually traverse streets, subtly lifting car…
-

The Security and Financial Advantages of an Outsourced SOC
In a recent article, “Why Outsourcing Cybersecurity is Essential for SMBs,” we explored the difficulties SMBs face when securing their digital assets against cyber threats and briefly discussed the pros and cons of building an in-house security operations center (SOC) versus using an outsourced SOC. In this follow-up post, we’ll take a more practical and…
-

Why Outsourcing Cybersecurity is Essential for SMBs
According to a study at the University of Maryland (Security Magazine) in 2022, a cyber attack occurs every 39 seconds. With the exponential growth of the threat landscape, cybersecurity cannot be a part-time job. It is certainly not a side hustle. Whether you are a global corporate giant or a local SMB, cybersecurity is not…
-

Why a SOC Has Become a Top Requirement for Cyber Insurance
It seems that everyone is trying to identify the next bubble to take some type of advanced action to avoid it or take advantage of it. Many of us have lived through more than one. There was the IT bubble at the start of the century followed by the housing bubble in 2008. Bubbles are…
-

Utilizing SOC Infrastructure vs Managed EDR – an MSSP perspective
The constant headlines concerning the latest attacks on companies across the industry spectrum serve as constant reminders of the importance of cybersecurity. Digital transformation alone is not enough. You must secure that digital environment, and it’s something that even SMBs have come to realize all too well. Unfortunately, most SMBs lack the technology stack, talent,…
Loading