The Evolution of SecOps: The Essential Components of MDR
As threat actors launch more sophisticated and AI-enhanced attacks, traditional preventative measures alone are falling short. Adequately protecting an intricate web of modern infrastructure — a blend of on-premise and cloud-based systems, numerous mobile devices, and many applications — while navigating increasingly stringent compliance regulations demands a more proactive and holistic approach.
Plenty of cybersecurity solutions are ready to assist, but choosing the right one often proves difficult. MDR, MEDR, XDR, EDR, SOC, SIEM, SOAR — it’s enough to make even a seasoned professional’s head spin. Each term represents a different aspect of security, with some being tools, others solutions, and many having overlapping or complementary features. This sea of letters creates misunderstandings, leaving a company vulnerable if the wrong solutions are implemented.
The recent upheaval in the Security Information and Event Management (SIEM) market, exemplified by IBM and others, is prompting decision-makers to reassess their security operations. Instead of simply replacing one SIEM with another, leaders have an opportunity to embrace a more comprehensive and cost-effective SecOps solution: Managed Detection and Response (MDR), which offloads much of the heavy lifting to a well-equipped and expertly staffed Managed Security Service Provider (MSSP).
This article will provide a high-level overview of the essential components of a complete MDR solution, demonstrating how they meet the security challenges of today and those that will emerge in the future.
The Future of Security Operations: Insights from TNO Research
According to recent research by the Dutch independent firm TNO, only businesses with unique risk profiles or those in vital sectors will be able to justify maintaining internal SOCs in the coming years. The escalating complexity and rising costs will render an in-house SOC impractical for most organizations. Instead, they will outsource their SOCs to MSSPs and reap the benefits of improved security capabilities without the operational burden.
TNO’s research predicts that future SOCs will emphasize proactive and predictive capabilities. By 2030, most security incidents will be detected and mitigated automatically using Security Orchestration, Automation, and Response (SOAR) tools and standardized security playbooks, although new or first-time-seen attacks will still require manual intervention, supported by AI tools. This shift will focus SOCs on optimizing situational awareness and proactive threat landscape monitoring, ensuring preparedness for upcoming attacks and the ability to implement preventative measures or minimize their impact. This strategic realignment underscores MDR services’ indispensable value, presenting organizations with a pathway to harden their defenses amidst an ever-evolving threat landscape.
Fundamental Components of an MDR Solution
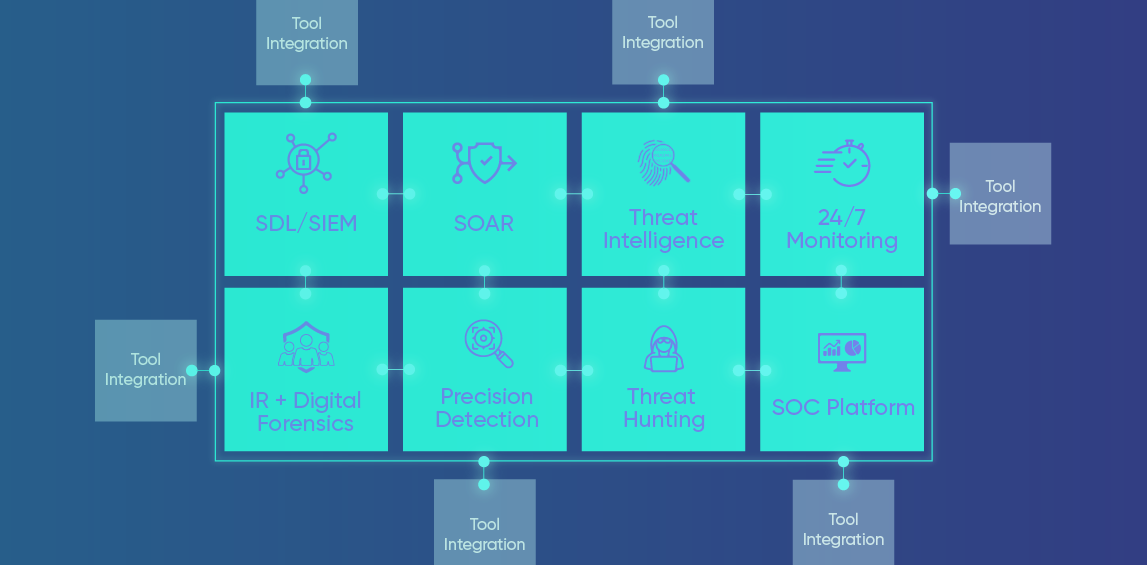
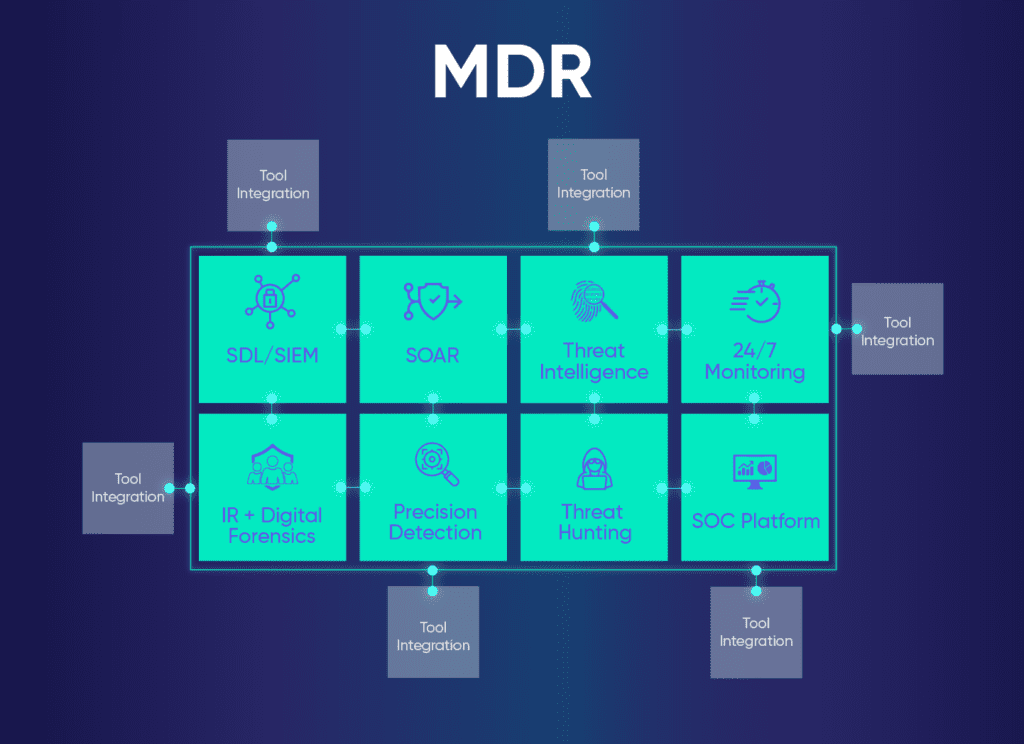
To safeguard expanding attack surfaces and complicated infrastructures, MDR solutions combine a set of foundational components; each plays a crucial role in providing comprehensive security coverage, ensuring that organizations can detect, respond to, and mitigate threats effectively.
Security Data Lake (SDL) or SIEM
The backbone of an MDR solution is an SDL or SIEM, both of which offer centralized logging and event management. While SIEM solutions were once the gold standard, today they struggle to meet the data needs of most organizations. SDLs take a more modern approach, enabling them to handle security analytics and immense data sets with limitless yet budget-friendly scaling capabilities.
Forward-thinking security leaders should opt for an SDL as data will continue to increase in future years, but this isn’t the only advantage of an SDL. An SDL enables comprehensive visibility into an organization’s IT infrastructure by correlating and analyzing security events from multiple sources, including networks, endpoints, cloud environments, applications, email, identity systems, and operating systems. Incorporating non-security log sources such as VMware vCenter provides valuable informational actions that enhance situational awareness. This unified view is necessary to identify anomalies, connect security events meaningfully, and comply with industry compliance regulations.
CYREBRO’s proprietary SDL is unique because it connects to every type of log-creating system and includes SIEM-like capabilities within a massive, scalable repository designed to address SIEM’s limitations.
Security Orchestration, Automation, and Response (SOAR)
SOAR is indispensable. It automates repetitive tasks such as threat detection, alert triage, and incident response (IR) actions and provides alert prioritization, threat investigation, IR playbooks, report generation, and case management. SOAR also orchestrates security tools, systems, and processes, improving communication, data sharing, and response times. Its multilayer automation technology delivers flexible automation capabilities that can be customized to meet various SecOps requirements.
Incident Response (IR/DFIR) Team
An IR team, including Digital Forensics and Incident Response (DFIR) specialists, is paramount for rapidly handling and mitigating security incidents. These experts respond to security breaches, implement containment measures, and ensure incidents are resolved efficiently to minimize damage.
Threat Intelligence Feeds
Integrating multiple threat intelligence sources from open-sourced, licensed, proprietary, and other feeds supplies an MDR with real-time updates on emerging threats and vulnerabilities, facilitating proactive defense strategies.
Advanced Precision-Detection
Leveraging machine learning (ML) and behavioral analytics, advanced precision detection capabilities allow MDR solutions to identify sophisticated threats, including unknown and zero-day attacks, while reducing false positives and noise so teams can focus on genuine threats.
Proactive Threat Hunting
Proactive threat hunting involves automated and manual searches for potential threats within the network, identifying and mitigating hidden or dormant threats that might evade traditional detection methods.
24/7 Threat Monitoring and Support
Continuous monitoring of the IT environment, coupled with expert SOC analysts, guarantees round-the-clock vigilance, professionals in identifying potential threats, and timely investigations.
Flexible Integration
Seamless integration with existing security tools and systems, alongside the capability to ingest, parse, normalize, and translate logs from any source into a unified schema using AI, ensures comprehensive coverage and compatibility.
SOC Platform
An interactive SOC platform provides a single pane of glass that centralizes all security operations, including alerts, threat detection, and investigations. It simplifies threat management with easy-to-follow recommendations in clear English.
Making Informed Decisions for Optimal Cybersecurity
Selecting the best security solution is a critical decision requiring a two-pronged approach. First, security leaders must accurately assess current security postures and capabilities, identify gaps, and consider future needs. Second, they must have a deep understanding of the types of solutions available and the nuances between similar offerings. Armed with this knowledge, organizations are better positioned to select solutions that not only maximize security but also keep costs manageable.
The journey towards enhancing cybersecurity resilience is never-ending, but an advanced MDR, complete with a Security Data Lake and the ability to connect to any log source, ensures that organizations remain one step ahead of today’s potential adversaries and those that will inevitably come in the future.


