Today’s Cyber Challenge: Multi-Site Security With a Diverse Tech Stack

In today’s globalized economy, it’s easier than ever for businesses to operate in multiple locations, with many crossing borders to reach a broader customer base. While this can bring many benefits, it can also create significant challenges, particularly when managing IT and cybersecurity.
As organizations increase their reach, they must work with service providers in their primary markets to avoid latency issues. With service providers spread across regions and varying technologies being used to accommodate an office’s unique needs, the overall IT environment becomes more complex; monitoring and maintaining cybersecurity measures becomes more challenging, leading to potential vulnerabilities.
With cyberattacks on the rise – 2022 saw a 38% increase from 2021 – and AI tools like ChatGPT able to write sophisticated code for hackers in seconds, it’s more important than ever for growing SMBs to harden their security postures.
Why are SMBs so appealing to hackers?
Hackers pay attention to the same “state of the industry” reports that security professionals read. Many repeatedly point out that SMB leaders know they are unprepared to mitigate attacks effectively because they have deprioritized security to focus more on financial growth. In a Q4 2022 survey, just 4% of SMB owners view cybersecurity as the biggest risk facing their company, and only 37% are concerned about becoming a victim.
Threat actors also know that as businesses expand and incorporate different technologies, systems, and tools across multiple locations, their attack surface grows, and smaller security teams struggle to detect and respond to threats quickly. Yet, like enterprises, SMBs hold valuable data such as customer information, financial data, and intellectual property that hackers can steal and monetize.
These facts add up to one thing: SMBs are soft, attractive targets. That’s why in 2021, 61% of SMBs were the target of cyberattacks, and 82% of ransomware attacks were against companies with fewer than 1,000 employees.
It seems like SMBs have their backs against the wall. They can’t stop growing. For practical reasons, they can’t require every one of their offices only to use a slim set of technologies. Even if SMBs could hire more security professionals, there is a shortage of qualified ones. This is a lot to overcome, but there are ways to do it.
How can SMBs regain control over their infrastructure?
While bringing on third-party solutions like a security operations center (SOC) can add to a business’s overall costs, they are very often a fraction of the cost of not having advanced cyber protection. SOCs can help SMBs cope with complex IT environments and respond to threats in several ways.
Centralize the management of dispersed tools and systems
An MSSP can act as a single point of contact for all security-related matters, helping to streamline communication, reduce complexity and give greater visibility into their security posture. They can also help companies consolidate their security tools and systems, which not only makes things more manageable but also helps cut costs associated with licensing, maintenance, and training. As businesses scale, MSSPs can match that by offering solutions that adapt to changing business requirements.
Ensure compliance standards
There is no universal set of compliance standards; every country has its own regulations, and industries within those countries may be subject to additional rules. New laws are being passed rapidly, making it nearly impossible for an SMB with offices around the world to stay on top of compliance standards.
MSSPs are well-positioned to help businesses meet all compliance standards due to their expertise, resources, and comprehensive approach to security management. They can provide regular reports and audits to ensure companies meet compliance requirements. If an issue arises, an MSSP can help remediate the problem by guiding and supporting the organization throughout the compliance process.
Correlate data for a single attack story
When a security incident occurs, it may generate multiple alerts across different security tools, each providing a separate piece of information about the attack often without an obvious connection. Without a single attack story, it can be challenging to piece together a complete picture of the incident, leading to a fragmented response and possible gaps in the investigation.
A SOC will correlate information and data from different security tools such as firewalls, intrusion detection/prevention systems, and endpoint protection solutions as well as non-security reporting systems to create a cohesive and accurate attack story. Using event correlation techniques, it can identify the relationships between security events and suspicious activities that might have gone unnoticed.
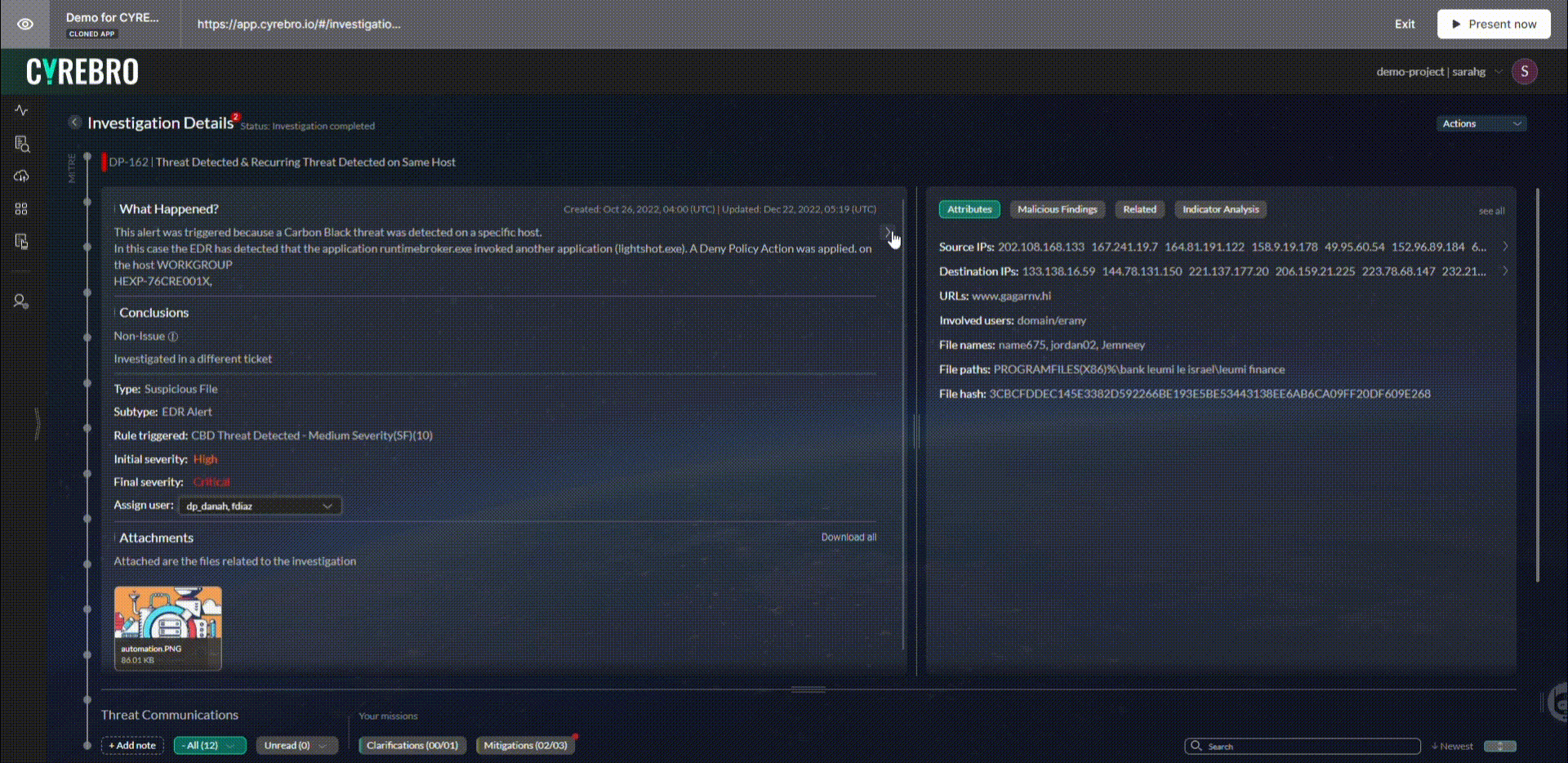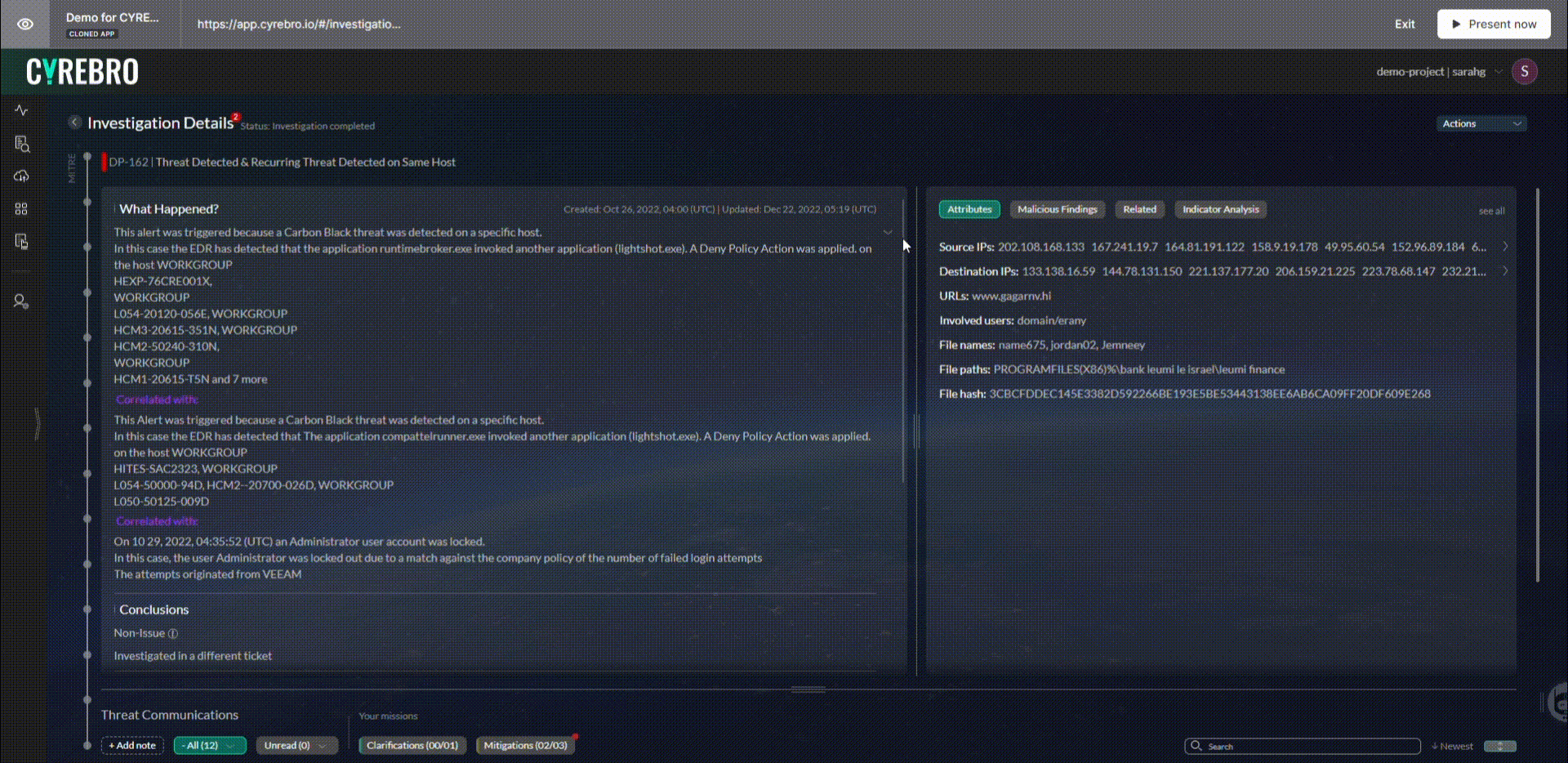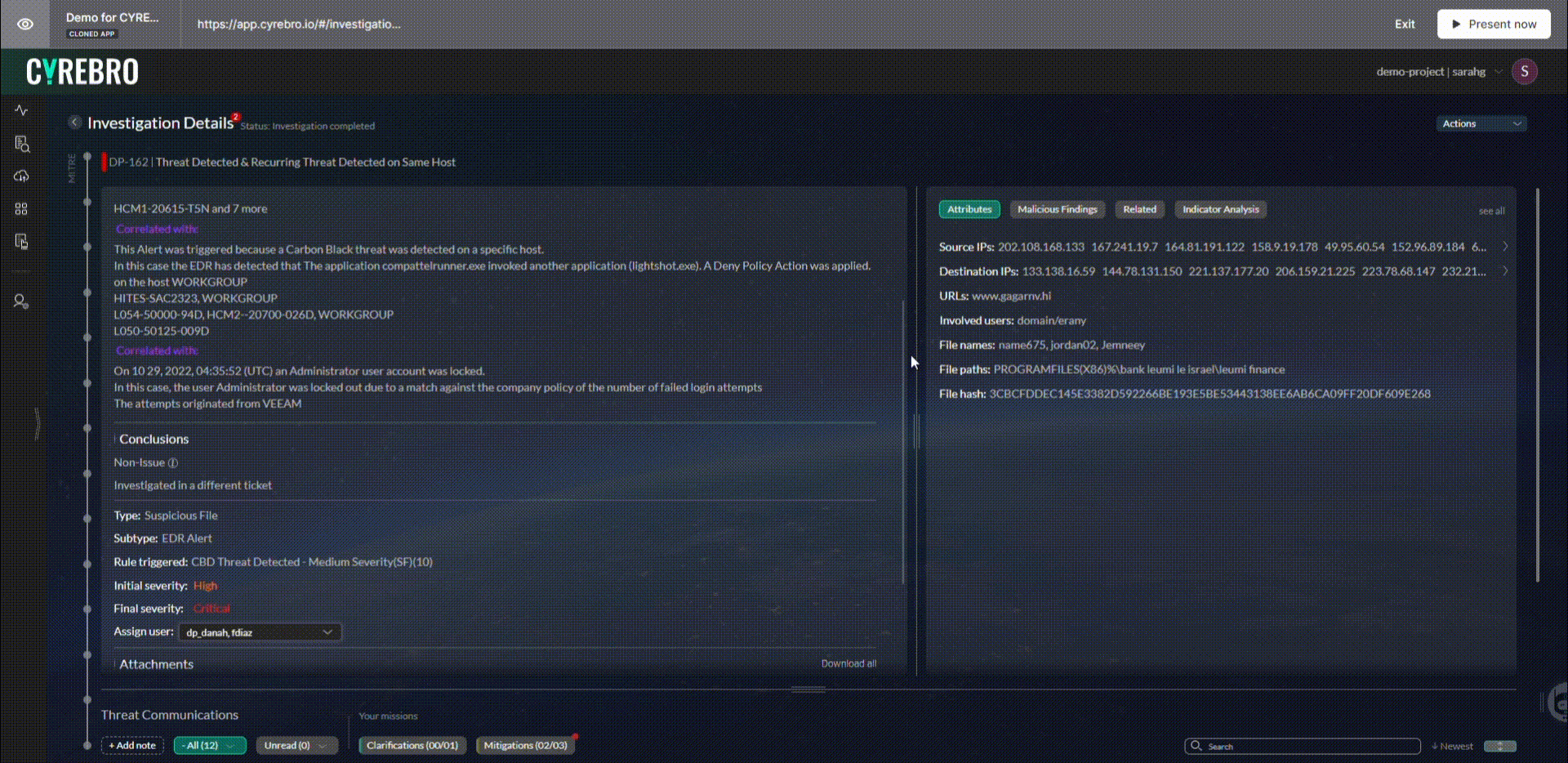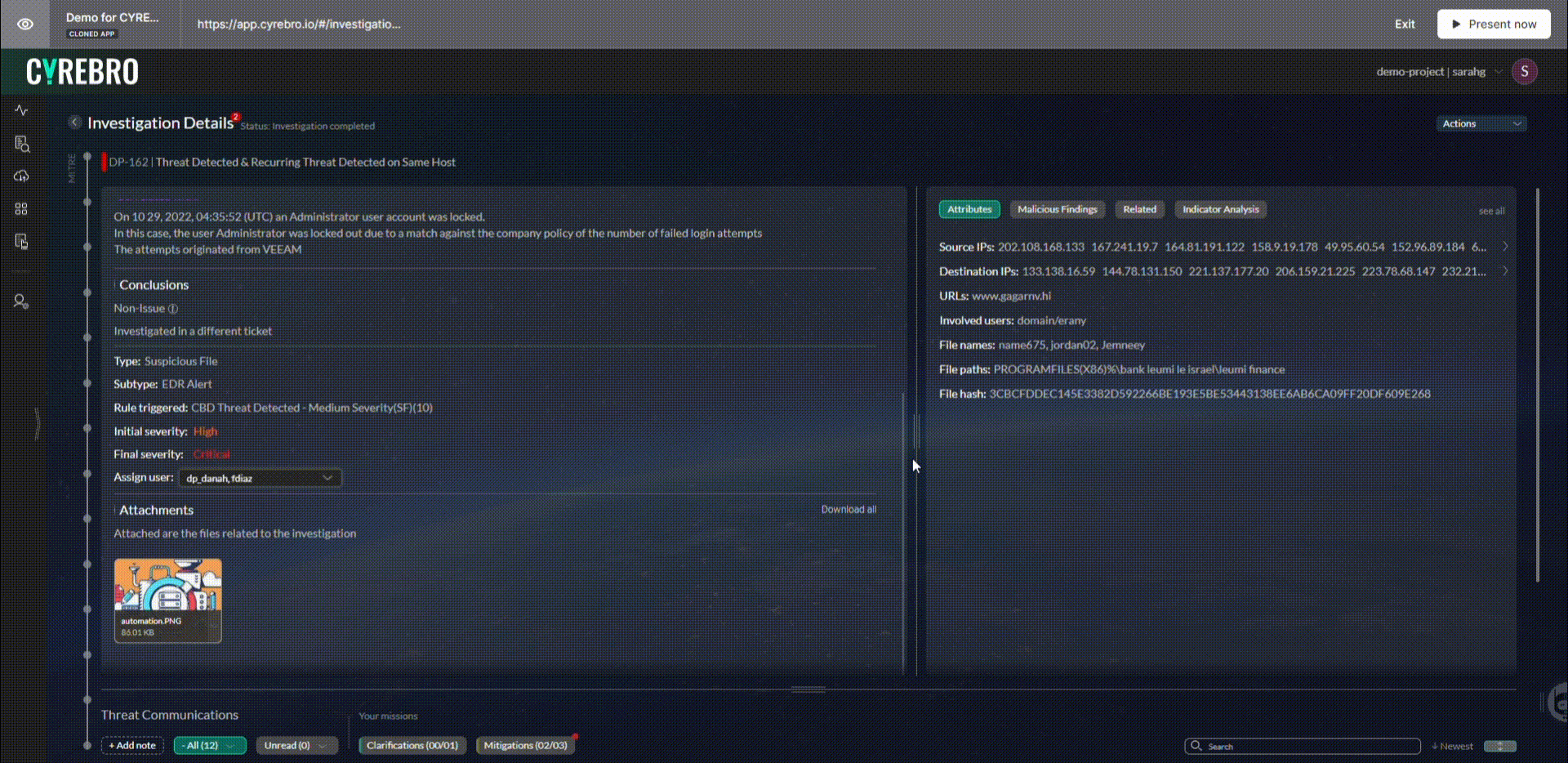
SMBs can also rely on SOCs to create an incident response plan and identify attackers’ tactics, techniques, and procedures (TTPs). When all this data is combined, SOCs can determine the extent of the damage and the necessary remediation steps.
A SIEM backed SOC for 24/7 monitoring and detection
A SOC’s 24/7/365 monitoring combined with a SIEM (security information and event management) for additional detection capabilities can provide proactive monitoring to prevent a security incident from occurring. However, should an attack happen, the SIEM back SOC can detect security incidents and enable SMBs to react in real-time, minimizing a threat’s impact.
Together, a SOC and SIEM generate a centralized view of security events across the IT environment, which helps SMBs manage and coordinate security resources, again reducing the risk of an attack.
Choose your partners carefully
For all the benefits a SOC and MSSP bring to an organization, they can also end up introducing risk or being detrimental if the partnership isn’t right. Any external vendor should be vetted. Those with nothing to hide should be open and upfront about their qualifications, internal security practices, and industry specialties.
Overcome security challenges with a SOC provider
Complexity and security are inversely related – the more complex a system becomes, the harder it is to secure because complexity creates a lack of visibility, making it challenging to identify vulnerabilities.
Multiple layers of software, hardware, and policies inevitably create blind spots threat actors are ready to exploit. SMBs should work towards continuously reducing their attack surfaces and enhancing their visibility, a process made infinitely easier by partnering with the right SOC and MSSP.
Although the tech world may appear interconnected, the reality is that organizations have traded simplicity for the appearance of “simple,” which actually hides a vast amount of complexity under the surface and makes it more difficult to address overall security.
A SOC delivers real-time monitoring and response capabilities so potential threats can be identified and addressed quickly. An MSSP supplies advanced security services beyond what most internal SMB teams can provide. By leveraging the expertise of a SOC providing MSSP, organizations can tackle the many security challenges that come with a growing global business.


